Key Takeaways
- The Problem: The August 2025 Windows update (KB5063878) enforces stricter User Account Control (UAC) for Windows Installer (MSI) repair operations, inadvertently causing unexpected prompts and blocking non-admin application installations for a wide array of software, including critical applications like Autodesk suites and older versions of Office (e.g., Office 2010).
- Immediate Fixes: For individual users, attempting ‘Run as administrator’ for affected applications can sometimes bypass the UAC prompt. For IT administrators in enterprise environments, Microsoft has provided a Known Issue Rollback (KIR) that can be deployed via Group Policy, though it requires contacting Microsoft Support for Business.
- Advanced Workaround: A targeted solution involves creating an elevated Command Prompt (CMD) shortcut. This shortcut leverages the native Windows Administrator account, allowing standard users to execute elevated commands after a one-time password entry. This method, while effective, carries inherent security risks due to the
/savecredflag. - Microsoft’s Stance: Microsoft officially acknowledged the issue on September 3, 2025, classifying it as ‘mitigated.’ While temporary workarounds are available, a permanent fix that will enable IT administrators to whitelist specific applications for MSI repair operations without triggering UAC prompts is currently in development. A timeline for this resolution has not yet been announced.
- Our Advice: We strongly recommend understanding the fundamental role of UAC in Windows security and avoiding its complete disablement. Instead, utilize temporary fixes judiciously, and for critical, recurring needs, carefully implement the elevated CMD shortcut workaround, always maintaining a clear awareness of its security implications. Stay informed about Microsoft’s progress towards a permanent, more elegant solution.
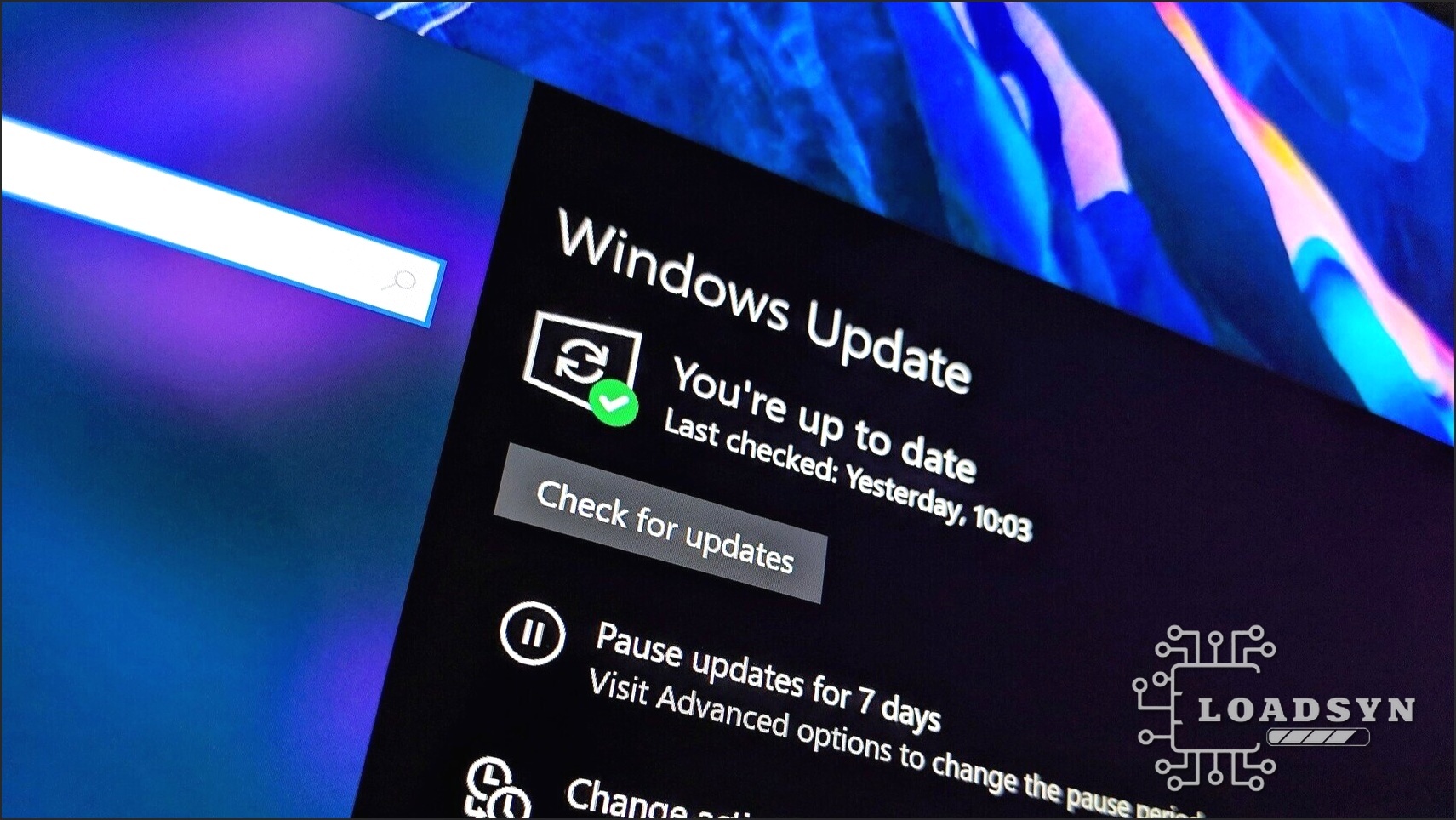
The August 2025 UAC Debacle: What Just Happened?
The digital landscape for Windows users, particularly those operating with standard accounts, has been significantly disrupted by Microsoft’s August 12, 2025, security update, KB5063878. While meticulously engineered to patch a critical privilege escalation vulnerability (CVE-2025-50173) by enforcing a more stringent User Account Control (UAC) for Windows Installer (MSI) repair operations, this cumulative update has inadvertently triggered a cascade of unexpected UAC prompts. For millions, a crucial security enhancement has, paradoxically, become a frustrating barrier, actively blocking routine application installations and vital software operations for non-administrator users across various Windows client and server versions. This unforeseen consequence has forced a re-evaluation of how standard users interact with their operating systems, creating a significant operational challenge.
- MSI Repair Operations: Any attempt to repair software via Windows Installer (e.g.,
msiexec /fu) now consistently triggers a UAC prompt, failing outright for non-administrators who lack the necessary credentials. - First-Time App Launches: Certain applications, most notably Autodesk software like AutoCAD, Civil 3D, and Inventor CAM, are now demanding UAC elevation upon first sign-in for standard users.
- Per-User Application Installations: Installing applications configured for individual user profiles often triggers UAC prompts, halting the installation process.
- Active Setup & ConfigMgr Deployments: Enterprise deployment processes that run Windows Installer during Active Setup or Configuration Manager packages relying on user-specific advertising are significantly impacted, leading to unexpected UAC blocks.
- Legacy Software: Older programs such as Microsoft Office Professional Plus 2010 now fail installation for standard users, presenting a definitive ‘Error 1730’ due to the heightened UAC enforcement.

UAC Explained: A Deep Dive into Windows’ Security Guardian
User Account Control (UAC), a cornerstone of Windows security since its introduction with Windows Vista, fundamentally reshaped how the operating system safeguards itself. Its core purpose is elegantly simple: to prevent unauthorized system changes by applications and users, effectively acting as a ‘protected mode’ that meticulously restricts access to Administrator privileges. Prior to UAC, malicious programs could freely manipulate system files, corrupt installed applications, or download/remove software without explicit checks, posing significant security risks. UAC mitigates this by automatically failing unauthorized write attempts to critical system paths and registry settings, requiring explicit user authorization—typically via a UAC prompt—for any action demanding specific device permissions. This ensures that only users with administrator privileges can grant or revoke such permissions, making modern Windows versions significantly more resilient and secure than their predecessors by meticulously protecting installed program files, user accounts, and core system registry settings.
A significant compatibility challenge emerged during UAC’s initial rollout, particularly with legacy 32-bit software that often required direct write access to system folders and registry entries. To bridge this critical gap, Microsoft engineered UAC Virtualization—an ingenious, security-centric solution. This technology effectively ‘fools’ non-UAC-compliant applications into believing they are writing to system paths, when in reality, an abstraction layer transparently redirects these write failures to a virtualized copy maintained within the user’s profile. This mechanism, which includes Registry Virtualization for system registry entries, creates a separate virtualized file copy for each user running the non-compliant app, thereby blocking access to global system components while enabling the software to operate. While primarily designed for 32-bit applications and requiring manual activation via Group Policy, UAC Virtualization was crucial for maintaining compatibility without sacrificing security. Although its relevance diminishes as software standards evolve and older applications become less prevalent, it remains a testament to Windows’ adaptive security architecture, ensuring older software could function within a more secure environment.
Navigating the Chaos: Your Actionable Solutions
Option 1: The Quick Fixes (Temporary)
- ‘Run as administrator’: For individual users encountering UAC blocks, right-clicking the affected application’s shortcut and selecting ‘Run as administrator’ can sometimes provide a temporary bypass. However, it is crucial to note that this option is frequently unavailable or ineffective for standard user accounts that genuinely lack administrative privileges.
- Known Issue Rollback (KIR) Policy (for IT Admins): Microsoft has developed a specialized Group Policy for enterprise environments to implement a Known Issue Rollback (KIR). This policy is specifically designed to suppress the buggy UAC prompts for certain Windows versions. IT administrators must contact Microsoft Support for Business to obtain and deploy this KIR. Microsoft strongly advises against disabling UAC entirely as a workaround, as this would reintroduce the very security vulnerability the August update aimed to fix, leaving systems exposed.
Option 2: The Elevated CMD Shortcut (Advanced Workaround)
For standard users who frequently encounter UAC blocks and require elevated permissions for specific applications without constantly involving an administrator, creating a specially configured elevated Command Prompt (CMD) shortcut can provide a targeted, albeit cautious, solution. This method ingeniously leverages the native Windows Administrator account to allow a one-time password entry, subsequently enabling the standard user to execute administrative commands without repeated authentication. This approach directly responds to the challenge of securely managing elevated privileges in a non-admin context.
- 1. Enable and Configure Native Administrator Account:
- Open an administrative Command Prompt (search ‘cmd’, right-click, ‘Run as administrator’).
- Execute:
net user administrator /active:yes(This command enables the hidden native Administrator account). - Lock your session (Windows + L). You should now observe an ‘Administrator’ user account as an option. Sign in to this account.
- Set a robust, strong password for this Administrator account: Navigate to Start > Settings > Accounts > Sign-in options > Password. This password is paramount for the shortcut’s security and functionality.
- 2. Identify Your PC’s Device Name:
- Go to Start > Settings > System > About. Carefully note down your ‘Device name’ as this will be a critical component in the shortcut’s target path.
- 3. Create the Elevated CMD Shortcut:
- Right-click on your desktop, then select New > Shortcut.
- For the target path, accurately enter:
C:\Windows\System32\runas.exe /user:YourPCName\Administrator /savecred "C:\Windows\System32\cmd.exe"(Crucially, replace ‘YourPCName’ with the exact device name identified in step 2). - Click Next, assign a descriptive name to the shortcut (e.g., ‘CMD Admin’), and click Finish.
- (Optional) Customize the icon for easier identification: Right-click the shortcut, navigate to Properties > Shortcut tab > Change Icon… (you can typically find suitable CMD icons within
C:\Windows\System32\shell32.dllorimageres.dll).
- 4. Configure Security Permissions for Standard Users:
- Right-click the newly created shortcut, select Properties > Security tab > Advanced.
- Click ‘Add’. Then click ‘Select a principal’, type the name of the target standard user account, and click ‘Check Names’ > OK.
- In the ‘Permissions’ tab, select ‘Allow’ from the dropdown. For security, check only ‘Read’ and ‘Read & Execute’ permissions for the standard user. Click OK.
- Apply and OK to close all open windows.
- 5. Deploy the Shortcut:
- Copy the fully configured ‘CMD Admin’ shortcut to the target standard user’s desktop (this is typically located at
C:\Users\<StandardUserName>\Desktop).
- Copy the fully configured ‘CMD Admin’ shortcut to the target standard user’s desktop (this is typically located at
- 6. Usage for Standard Users:
- When the standard user double-clicks the ‘CMD Admin’ shortcut, they will be prompted to enter the password previously established for the native Windows Administrator account (from step 1). For security, this password will not be visibly displayed as it’s typed.
- Crucially, the password only needs to be entered once. Thanks to the
/savecredflag, subsequent executions of the same shortcut will automatically run with administrative permissions without requiring re-entry, streamlining operations for the standard user.
Microsoft’s Official Response & The Road Ahead
Microsoft officially acknowledged the widespread User Account Control (UAC) issue on September 3, 2025, classifying it as a ‘mitigated’ problem. The company unequivocally emphasized that the underlying security improvements, introduced by KB5063878 to patch the critical CVE-2025-50173 vulnerability, are necessary and strongly advises against rolling them back by disabling UAC. While temporary workarounds such as ‘Run as administrator’ and the enterprise-focused Known Issue Rollback (KIR) Group Policy are currently available, Microsoft is actively developing a comprehensive, permanent fix. This future Windows update is expected to provide IT administrators with the crucial capability to whitelist specific applications, thereby allowing them to perform MSI repair operations without triggering UAC prompts for standard users. However, a specific timeline for the release of this resolution has not been announced, leaving many users and IT departments reliant on the current, often inconvenient, workarounds.
The KB5063878 UAC Update: A Double-Edged Sword
Pros
- Enhanced Security: Successfully patches CVE-2063878, preventing local privilege escalation through weak Windows Installer authentication, significantly bolstering system integrity.
- Stronger UAC Enforcement: Reinforces the principle of least privilege, making it substantially harder for malware or unauthorized processes to make system-wide changes without explicit administrative consent.
Cons
- Widespread Usability Issues: Causes unexpected UAC prompts for standard users across a broad range of Windows versions, severely disrupting legitimate application installations and operations.
- Application Compatibility: Breaks critical functionality for specific, widely used software (e.g., Autodesk suites, Office 2010) and prevents standard users from performing essential MSI repair processes.
- User Frustration: Leads to significant user fatigue and, in some cases, prompts the adoption of workarounds that, if not implemented with extreme care, could inadvertently compromise system security.
Frequently Asked Questions About UAC & The August 2025 Update
What is User Account Control (UAC)?
UAC is a fundamental Windows security feature introduced with Windows Vista. Its primary function is to prevent unauthorized changes to your operating system by requiring explicit permission—often an administrator password—before an application can make modifications that affect other users or the system’s core security. This effectively restricts access to administrator privileges, ensuring greater system integrity.
Why is KB5063878 causing UAC issues?
The August 2025 update, KB5063878, introduced stricter security enforcement for Windows Installer (MSI) repair operations. This was a deliberate measure to patch a critical privilege escalation vulnerability (CVE-2025-50173). However, this new, stricter enforcement now triggers UAC prompts even for routine MSI-based operations when performed by standard users, effectively blocking them without administrator credentials.
Is it safe to disable UAC completely?
Microsoft strongly advises against disabling UAC entirely. While it might resolve the immediate prompt issues, doing so would reintroduce the very security vulnerabilities the update aimed to fix. This leaves your system significantly more susceptible to malware, unauthorized changes, and a range of security risks.
Will Microsoft release a permanent fix?
Yes, Microsoft has officially acknowledged the issue and is actively working on a comprehensive, permanent fix. A future Windows update is expected to provide IT administrators with the capability to whitelist specific applications for MSI repair operations, thereby preventing UAC prompts without compromising security. However, no specific timeline for this resolution has not been provided.
Are there any gaming-specific impacts?
While not explicitly detailed for specific games, any game launcher, anti-cheat software, or game-related utility that relies on Windows Installer for repair, updates, or initial per-user installations could potentially be affected by these UAC changes. This could lead to unexpected prompts, installation failures, or operational disruptions for standard users attempting to manage their gaming software.
Final Verdict
The August 2025 UAC update, KB5063878, presents a classic dilemma in system engineering: enhanced security versus immediate usability. While Microsoft’s intent to patch a critical privilege escalation vulnerability is commendable and fundamentally necessary, the execution has unfortunately created significant friction for millions of standard Windows users. As LoadSyn.com’s technical bedrock, understanding the frustration when core system functions impede your ability to install or maintain software is paramount. Our recommendation is to prioritize security by unequivocally avoiding a complete UAC disablement. Instead, leverage the temporary workarounds like ‘Run as administrator’ for occasional needs, and for critical, recurring scenarios, carefully consider the elevated CMD shortcut workaround, fully internalizing its significant security implications. Stay vigilant for Microsoft’s promised permanent fix, which should ultimately provide a more elegant solution for managing elevated privileges without sacrificing essential user experience. Until then, navigate these complex waters with caution, informed choices, and a keen eye on system integrity.
Key Intelligence Briefs & Microsoft Documentation
- Microsoft Q&A: ‘Autofill UAC Prompt to Input Username and Password Admin with Batch Scripting’
- Microsoft Support: KB5063878 (August 12, 2025 — OS Build 26100.4946)
- Microsoft Support: CVE-2025-50173 Security Vulnerability Details
- Microsoft Security Baselines: Windows 11, version 24H2 Release Notes
- Windows SDK for Windows Vista Beta 2 Documentation (UAC Manifests)
- Bitdefender Support & Community Discussions (Remote Scan Behavior on Windows vs. macOS)
- UAC (User Account Control) & DEP (Data Execution Prevention) for Alliance (08/09/11)